Countermeasure for password function vulnerability of PLCs
1. Overview
A vulnerability has been discovered that could allow a remote or local third party to steal passwords when using the password function in our PLC products.
If you are using the password function of the relevant PLC, please check the contents and take the following measures.
2. Vulnerability
Vulnerability 1: Responding to confidential information via serial communication
The PLC is vulnerable to specially crafted communication commands to the serial communication port.
This causes the PLC to return password information.
CWE ID: CWE-319
CVE ID: CVE-2022-2003
CVSS v3 AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N Base score: 7.7
Vulnerability 2: Responding to confidential information via Ethernet communication
The PLC is vulnerable to specially crafted Ethernet packets via the PLC’s built-in Ethernet port or ECOM module.
This causes the PLC to return password information.
CWE ID: CWE-319
CVE ID: CVE-2022-2004
CVSS v3 AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N Base score: 7.5
3. Impact
If a password or other information is intentionally stolen using this vulnerability, it may lead to the theft of PLC programs, leakage of confidential information of the equipment or machinery, or unauthorized operation of the equipment.
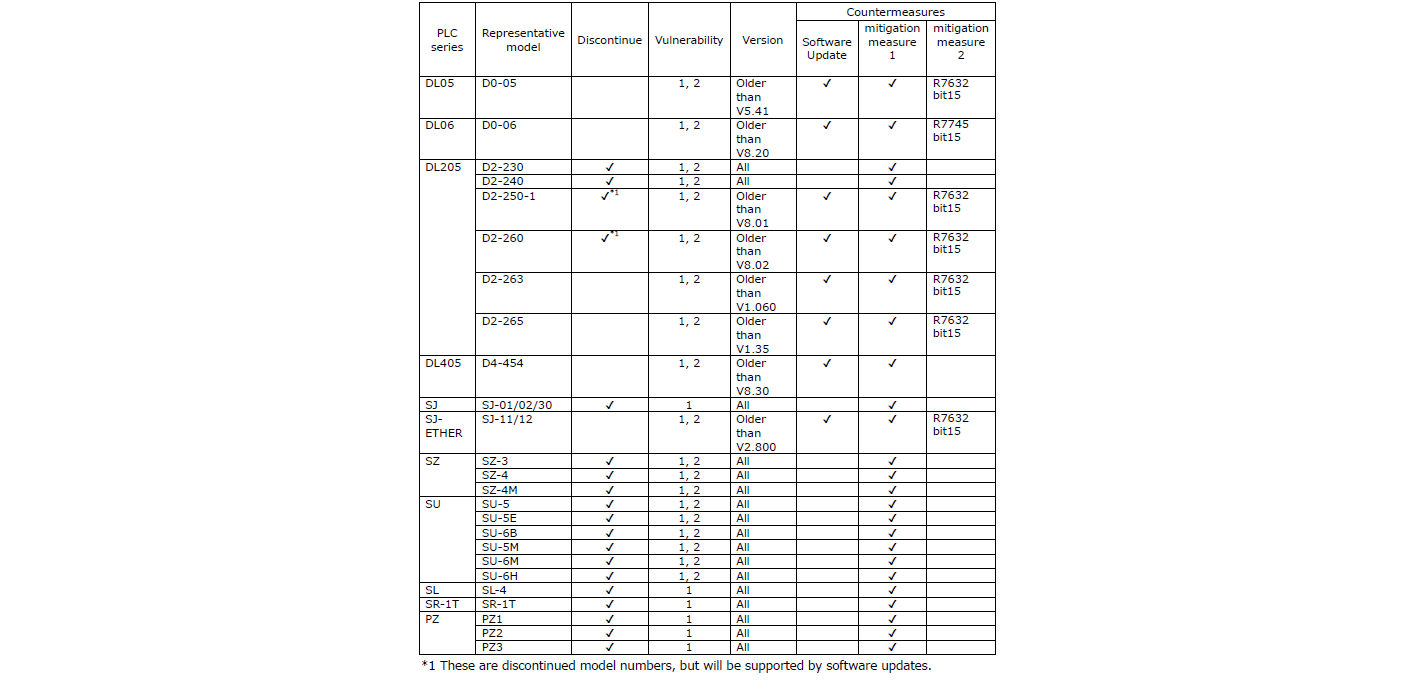
4. Countermeasures
PLC series currently available can be made countermeasures with updating its software.
If software updates cannot or will not be performed, a combination of Mitigation Measure 1 (described below) and Mitigation Measure 2 (for some models) can be used to reduce the impact of the vulnerability.
For information on software updates, please contact us.
Inquiries Concerning Technical Issues
For PLC series that have already been discontinued, the impact of the vulnerability can be reduced by the following Mitigation Measure1.
Mitigation Measure 1:
For Ethernet communication, do not connect to external network, but only to a secure local network, or connect to a secure network isolated by a firewall.
Mitigation Measure 2:
When setting a password on the PLC, do not leave the password open.Lock it with the password and turn ON bit 15 of the designated register for security enhancement to prohibit reading of the password (depending on the PLC model).
In addition if there are no devices connected to the communication port and the port is physically locked to prevent unspecified persons from accessing unused ports, there is no need to take countermeasures by updating the software.
No software countermeasures are required if the password function is not used.
5. Target PLC series
The countermeasures should apply to the following PLC series when the password function is used.